Customized solutions focused on the client

Customized solutions focused on the client

Quality assurance

Software testing
Access the planning and execution of functional, performance, load, stress, manual, and security tests to identify and correct software defects.
Accessibility testing
Ensure that the software is accessible to people with disabilities. At Wigilabs, we evaluate compatibility with screen readers, keyboard navigation and other accessibility criteria.
Software quality management
Establish quality standards, processes and methodologies to ensure the final product’s quality. Additionally, access the implementation of practices such as code reviews, static and dynamic analysis and quality assurance.
QA-Ops Methodology
QA-Ops ensures 98% quality and software operation, focusing on achieving the best quality with a DevOps approach. QA-Ops operates under the DevSecOps methodology. Our model aims for QAteams to work alongside the development team to achieve the required quality for each digital asset. In this way, we ensure that the result of each test meets the requirements, and we focus on finding as many defects as possible before the deployment of any asset.

Process improvement consulting
We advise you on improving software development processes by incorporating agile practices, DevOps, and other approaches that promote quality and efficiency
User Experience (UX) Testing
Evaluate the usability, navigation and overall user experience of your software.
Test Automation
Develop scripts and tools to automate
testing and improve the efficiency and repeatability of functional and regression tests.

Best practices in test execution


Structure and guidelines
Planning
We receive and study the documentation to prepare for testing.
Analysis
We understand what should be tested and with which resources.
Design
We analyze each scenario and its preconditions.
Construction and testing
We prepare the necessary tools to execute each test, recording the results.
Closure
We report the tests and determine if everything has been satisfactory.

Ethical hacking
We Evaluate the Security of Your Systems
We include penetration testing, vulnerability analysis, reverse engineering and physical security assessments. These techniques are used to detect weaknesses in your organization’s ITinfrastructure, such as configuration errors, outdated software, unsecured open ports, weak passwords and more.Take corrective actions
Once these vulnerabilities are identified, inform the system owners or security personnel so they can take corrective measures and strengthen the security of their systems. This practice helps protect confidential information, prevent cyberattacks and improve the overall security posture.

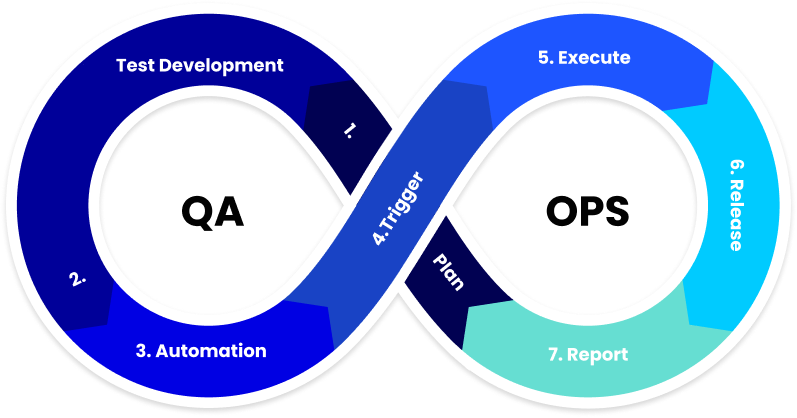
We build a sustainable and systematic Engine

Understand the correct functioning of each deliverable

Ethical hacking
dentify flaws and prevent defects.
Reduce risks or failures.
Identify the source of errors, defects or failures.

Related Cases














